07.09.2023
1
Beğenme
57
Görüntülenme
Definition of Diamond Model, MITRE ATT&CK® comparisons and pros&cons.
INTRODUCTION
Intrusion analysis is very important in cyber threat intelligence. It is especially vital in terms of early detection of threats before they cause a problem and its measures that can be taken during a threat. This essay explains frameworks and concepts that are very useful in intrusion analysis. These are; Diamond model, Cyber Kill Chain and Mitre ATT&CK® Framework. It then describes their common and different aspects. Subsequently, compare the pros and cons with each other.
1-)DIAMOND MODEL:
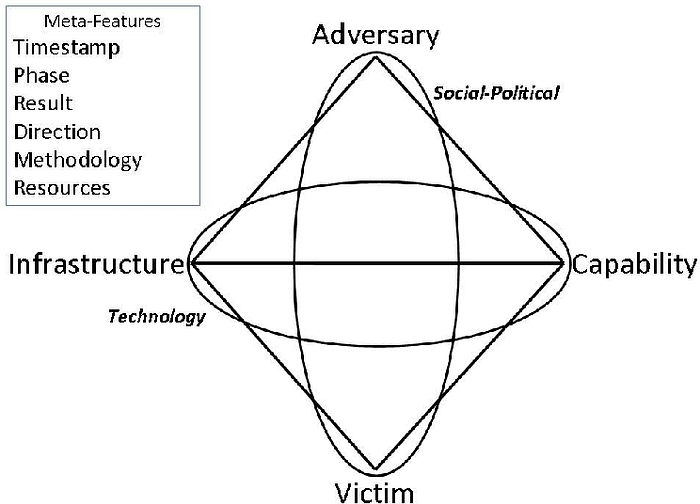
The Diamond Model is a Intrusion Analysis Framework for researching and analyzing cybersecurity incidents. It is made up of four major components: adversary, victim, capability, and infrastructure. In addition, why is it called a “Diamond Model”?. The four core features are edge-connected and arranged in the shape of a diamond to highlight their underlying links. Let us now go over these components in further detail.
a) Adversary
An adversary may also be referred to as an attacker, an enemy, a cyber threat actor, or a hacker. The adversary is the person or entity responsible for the cyberattack.
b) Victim
Victim is the target of the adversary. Victim can be a company, person, IP address, domain, etc.
c) Capability
Capability is an adversary’s tools, skills, techniques and talents. The capability focuses on the adversary’s structure.
d) Infrastructure
Infrastructure can be defined as the software and hardware used by the attacker.
Event Meta Features
There are six meta-features can added to the model.These are not necessary, but they add important information to the model.
-Timestamp: It is the occasion’s day and time. An event’s time and date of occurrence can be recorded
- Phase: The stages of an intrusion, attack, or breach are as follows.
-Result: Recording all of the post-event circumstances, such as details gathered during the reconnaissance phase or successful password or sensitive data exfiltration.
-Direction: This helps describe host-based and network-based events and represented the directions of the intrusion attack.
-Methodology: General classification of intrusions.
-Resources: Software, knowledge, information, etc.
In conclusion, by evaluating these components and developing a more effective response, analysts can gain a thorough picture of the attack.
2-)MITRE ATT&CK®:
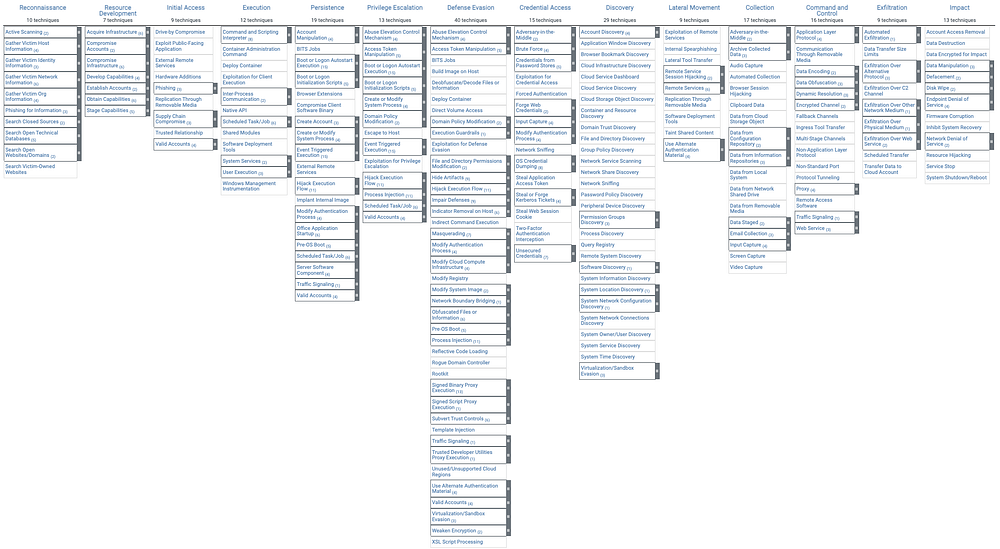
MITRE ATT&CK® stands for MITRE Adversarial Tactics, Techniques, and Common Knowledge(ATTA&CK). It is a knowledge base used to make adversary techniques and tactics accessible worldwide. It is used worldwide across multiple disciplines like; intrusion detection, threat hunting, security engineering, threat intelligence, red teaming, and risk management. In addition, it is necessary to mention ATT&CK Matrix. Contains 14 different categories and each category contains the techniques an adversary could use to perform the tactic.
a)Reconnaissance: Gathering information about a target
b)Resource Development: Establishing resources to support operations
c)Initial Access: Try to get victims network
d)Execution: Try to run the malicious software on the victim’s machine/server.
e)Persistence: Try to maintain foothold and changing configurations
f)Privilege Escalation: Elevate permissions to higher levels.
g)Defense Evasion: Attempting to evade detection
h)Credential Access: Try to steal credential information like usernames, passwords etc.
i)Discovery: Attempting to understand machines and what adversaries can do.
j)Lateral Movement: Move through on the victim’s machine..
k)Collection: Stealing and collecting data, files from victims
l)Command & Control: Try to control the system..
m)Exfiltration: Moving data to a cloud account.
n)Impact: Manipulating, disrupting and eradicating systems and data.
COMPARISONS:
MITRE ATT&CK is a little more static and multi-staged compared to the Diamond Model. These stages are very precise and the events that can happen within the steps are predictable. Especially, MITRE ATT&CK includes tactics, techniques and tools used in past attacks. In this way defenders can learn how to defend themselves more easily and make their systems much more stable.
Diamond Model was developed to track a thread actor across numerous intrusions. Because this model does not depend on any attack experience. Although it seems basic, the Diamond Model understanding of how attacks can happen involves many phases between its sections.
PROS & CONS:
Diamond Model Cons:
-No examples of previous threads.
-Look basic and not cover all topics.
-More focused on analytics than processes.
Diamond Model Pros:
-Easily understandable.
-Cover the approach not example.
-Useful in grouping intrusions for analysis.
-Complementary the other frameworks.
Yorumlar
Kullanıcı yorumlarını görüntüleyebilmek için kayıt olmalısınız!
Barbaros Kılıçarslan
Responsible, hardworking, and detail-minded. I can handle working under pressure and communicate and collaborate seamlessly in a team. My passion for security stems from my curious and persistent nature, constantly learning through all resources. Proficient with; IT management, Network Fundamentals, and Linux. And also adequate coding experience. I seek a position to develop information security architectural techniques, mitigate company cyber risks, and build a career in Information Security.
Konum
İstanbul, TR
Eğitim
Jeofizik Mühendisliği - İstanbul Teknik Üniversitesi
Yönetim Bilişim Sistemleri - İstanbul Üniversitesi
İş Tecrübesi
Cyber Threat Intelligence Analyst | External Attack Surface Management Analyst - Threatmon